The Personal Information Management Practices of the Graduates of the Department of Information Studies at Kuwait University
Abstract
This study examined activities involving the finding, organizing, managing, and re-finding of information by knowledge workers in Kuwait. This research also conducted a review of the tools needed for effective personal information management (PIM) and assessed perceptions about improving PIM through Internet use. Data were collected through semistructured interviews conducted among 26 graduates of the Department of Information Studies at Kuwait University. These participants are currently employed in different sectors engaged in a variety of information-related activities. This study’s findings indicated that participants gathered different types of information from a variety of sources. This information was stored using several devices and services, including desktop computers, shared drives, clouds, bookmarked websites, e-mail correspondence, and favorites lists. Participants organized information in personal folders according to categories such as subject/topic, time, project, document type, and geographical region. Preferred methods for information re-finding included searching by keyword and browsing through folders. Interviewees reported problems of information overload, fragmentation, and anxiety. Most were active in social media via mobile device, while some of them used Siri or Ask Google to retrieve information. Tools used for PIM included calendars, tasks, schedules, e-mail management tools, clouds, and social networking tools. Participants reported that the Internet helped with personal information management practices, but that some privacy issues arose in this context.
Keywords:
Personal Information Management, Knowledge Workers, Information Finding, Information Organization, Information Management, Information Re-finding1. Introduction
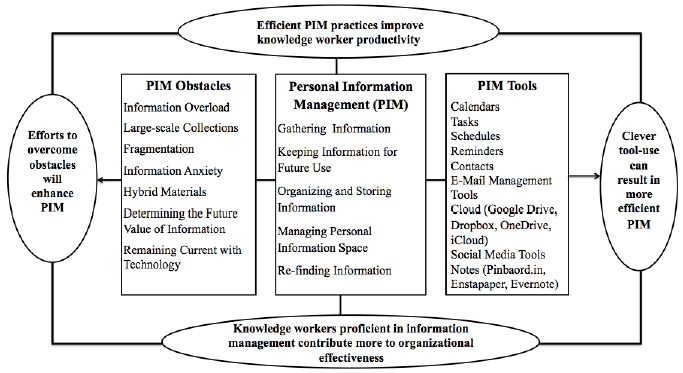
Personal Information Management (PIM) has been defined “as both the practice and the study of the activities people perform to acquire, organize, maintain, retrieve, use, and control the distribution of information items such as documents (paper-based and digital), web pages, and email messages to complete tasks and to fulfill various roles” (Molazadeh et al., 2017, p. 108). Information management begins by finding new information. Keeping useful information while excluding the non-essential from the personal information space is another core PIM activity. Saved information is organized by tagging, categorizing, and storing it in digital folders. PIM requires regular maintenance that includes deleting, adding, and updating information. Re-finding information is considered the ultimate goal of PIM that involves information retrieval. There are many PIM tools and technologies designed to facilitate these practices, including calendars, e-mail management applications, tasks, schedules, search functions, and social networking services.
Information overload is one of the most common difficulties encountered when performing PIM. It occurs when time restrictions prohibit users from organizing and evaluating the available information. Information overload can thus lead to information anxiety and the need to substantially rely on the human memory, which may result in frustration, distraction, confusion, helplessness, irritation, and annoyance (Chaudhry, Rehman, & Al-Sughair, 2016). Another difficulty involves managing files on different devices and migrating them to alternate formats, a process otherwise known as information fragmentation. Hybrid materials (i.e., those composed of both traditional and electronic formats) can also result in difficulty when searching for information. However, these difficulties can be overcome through efficient information management behavior. Appropriate PIM strategies can also mitigate these problems. For example, this involves cleaning, managing, deleting, and updating electronic files. Information overload can thus be reduced to facilitate efficient re-finding.
1.1 Problem Statement
An overwhelming amount of information has become available during the digital era. Determining the value of this information and gathering what is needed for both personal development and organizational effectiveness is becoming a challenge for knowledge workers. It is thus important to investigate how knowledge workers in different organizations manage, organize, keep, and re-find information. This study investigated the PIM practices of knowledge workers in Kuwait. The following sections describe the activities performed by a group of knowledge workers when gathering, organizing, managing, and re-finding information. This study also explored the use of PIM tools and Internet services to facilitate PIM practices.
1.2 Research Questions
The following questions guided this study:
- 1. What information (i.e., e-content) types are required to complete work tasks?
- 2. What activities are performed during personal information management?
- 3. What tools are used while managing personal information?
- 4. How does the Internet facilitate PIM practices?
2. Literature Review
Chaudhry, Rehman, and Al-Sughair (2015) studied the information strategies used by employees of private companies in Kuwait. Results indicated that information was gathered using company resources, social media platforms, and websites. Employees saved important information using e-folders, bookmarks, and favorites lists in web browsers. E-documents were organized according to work task and divided into groups. Employees also frequently searched by file name and used bookmarks to re-find information.
Molazadeh et al. (2017) studied the PIM activities performed by faculty members at three universities in Iran by focusing on four aspects (i.e., acquisition, maintenance, organization, and retrieval). Their findings showed that 75% of participants used PIM tools and that most preferred desktop computers for saving work-related information. Kearns et al. (2014) examined faculty members who conducted online courses as part of the Web-based Information Science Education (WISE) Consortium. Participants managed information using e-mail, desktop computers, web-based information systems, and learning management systems. While information overload is usually a significant issue, the main problem experienced during information management in this case was “filter failure.”
Divya and Sudhier (2016) studied attitudes about PIM among research scholars in the Faculty of Applied Sciences at the University of Kerala. Respondents reported difficulty when updating information, but had above-average information searching and maintenance skills. Al-Omar and Cox (2016) examined the practices of scholars in the department of Education and Health Sciences at a Kuwaiti higher education institution. Their findings indicated that scholars’ research-related personal information collections were supplemented with new information throughout the research life cycle. The collections were thus huge, diverse, hybridized, and fragmented. Key factors resulting in these problems were research pressures, limited time, quality of available space, lack of technology opportunities, lack of support from central services, requirements to collect Arabic material, self-presentation, and self-management.
Diekema and Olsen (2011) studied the PIM practices of schoolteachers. Results indicated that participating teachers were aware of different information sources (e.g., digital libraries and school media centers), but did not use them. Information was managed alphabetically, topically, and by educational standard. Teachers stored information in a variety of ways (e.g., physical storage in cabinets, closets, and shelves). They also utilized digital computer storage, school group drives, and bookmarks. The authors also discovered the phenomenon of “information heritage,” meaning that teachers took information from their predecessors and used it when performing PIM.
Many companies offer a variety of Internet-based services (e.g., Gmail, Yahoo, Hotmail, Google Apps, Office Online, Facebook, and MySpace). Many of these services also include functions that provide storage space to account users for managing personal information. Majid et al. (2010) studied university student usage of these services when performing PIM. Very few participants reported using online storage to maintain information about appointments, telephone numbers, drafted documents, audio and video recordings, or to-do lists. However, most students used other Internet services to store and manage personal information, including e-mail correspondences and personal texts containing documents and photos. On the other hand, over two-thirds of all respondents stored non-sensitive personal information in online storage accounts. This is because they were not as concerned about the privacy and security of such information.
Otopah and Dadzie (2013) studied student PIM practices in addition to their implications for library services at the University of Ghana. Students employed different document formats (i.e., both paper and non-paper based), computing skills, collection sizes, memory types, and habits during PIM. These findings showed indicated problems of inadequate skills, information fragmentation, inappropriate habits, and imperfect memory. A similar study was conducted by Mizrachi and Bates (2013). Their findings revealed that students exhibited both creativity and variety in their use of both automated and manual resources and other devices used to support their academic work. These results provided insights into both PIM and the overall planning and management practices preferred by students.
Bota et al. (2017) studied e-mail as a common PIM tool. Participants reported using self-addressed emails (i.e., self-Es) to support information management. Most self-Es were used to store task lists and reminders. Researchers found that URLs, images, quotes, travel directions, and phone numbers had longer lifespans because of metadata use (e.g., flagging content), which facilitated the search process. Zhou, Mohammed, and Zhang (2012) reviewed the use of other tools, including task and contacts lists. They then proposed a mobile personal information management agent (PIMA), which was designed to improve mobile PIM through a natural language interface, application integration support, and the ability to overcome physical constraints. Prototype testing indicated that the PIMA improved perceived usefulness, ease-of-use, and efficiency on mobile devices.
Kim and Hur (2016) studied how PIM tools, personal information sensitivity, and information ethics awareness affected information security awareness. They found that information security awareness did not have a significant relationship with personal information management tools or Internet usage time. On the other hand, information security awareness had a significant relationship with personal information sensitivity and information ethics awareness.
The above literature review served as a basis for this study’s conceptual framework, which is illustrated in Fig. 1.
3. Research Design
Semi-structured interviews were conducted to collect the data used in this study. This process was based on relevant previous studies using either the survey method, personal interviews, or both (Majid et al., 2010; Al-Omar & Cox, 2016; Creegan, 2017; Chaudhry, Rehman, & Al-Sughair, 2016).
This study focused on knowledge workers in different organizations in Kuwait. The term “knowledge worker” in this study refers to a professional with a minimum of a graduate degree who works in a knowledge-intensive environment. This study’s participants were graduates of the Department of Information Studies at Kuwait University who completed master’s degrees in either library and information science or information studies. The department provided a list of graduates containing over 200 names, email addresses, and phone numbers. Some names were listed without contact information, while others were only accompanied by one contact method. All graduates were invited to participate in the study using e-mail correspondence containing a cover letter that described the scope of the study.
Many of the listed e-mail addresses were not active as evidenced by returned mail messages the mail delivery system. However, those who replied and agreed to participate in the study were sent an interview guide. Short semi-structured interviews lasting between 15-30 minutes were then conducted in person or by phone (some participants were outside Kuwait at the time) on an individual basis. A total of 26 interviews were conducted. The interview guide disseminated to participants is available in Appendix A. The guide was used as a template; additional questions and/or clarifications were provided to prompt participants to provide relevant information. Some participants pointed out issues that were not included in the interview guide. Most participants were aware of the main study concepts and had relatively little difficulty responding to the questions. All participants were willing to be contacted at a future time if more questions developed. The collected information was coded using serial numbers and participant initials. Interview contents were analyzed according to the following themes: Information gathering, keeping, organizing, managing, obstacles, re-finding, using the Internet, and mobile devices. Answers to some questions were grouped to fit listed themes.
4. Discussion
Participant demographics are presented in Table 1. Participants worked in different locations and had different educational backgrounds (i.e., different undergraduate majors were accepted to the master’s program in the Department of Information Studies). However, all participants had master’s degrees from the Department of Information Studies at Kuwait University.
All participants were employed in jobs dealing with different aspects of information. Most participants were administrative assistants, a job which requires awareness of the importance of PIM. Some participants assisted university academic departments, while others were involved in project assessments at different institutions (e.g., the United Nations (UN), Kuwait Oil Company (KOC), and public sector organizations such as the Central Agency for Public Tenders). The second most common work role among participants was that of schoolteacher. Some schoolteachers held supervisory positions, while others were department heads or vice principals. A smaller number of participants were information specialists, social workers, trainers, or software programmers. Although participants worked in different roles in many organizations, all were qualified as professionals in information management. Appendix B provides further details. Participant names were not listed to retain anonymity.
4.1 Gathering Information
The term “personal information” as used in this study does not refer to information about participants. Rather, it is used to refer to the types of e-content that an individual knowledge worker collects or receives during work. Participants reported that they gathered information according to the work task and user need of those they assisted. Most participants used online databases and journals. Some reported dissatisfaction with institutional resources. For example, one participant stated the following: “I use Google to find information and I do not use the school library because it does not provide the information for teachers.” Many teachers reported difficulty with library collections because they were organized around specific subject areas instead of new teaching methods. This corroborated research by Diekema and Olsen (2011) in which teachers reported not using library resources. They instead relied on colleagues, databases, and teacher forum archives. Information specialists had more practical ways of gathering information. For instance, one participant stated the following: “SurveyMonkey, social media especially Instagram bio, group discussion, and lab observation are used for collecting data.” Health information specialists used the Kuwait Heath Annual Book, patient consultation system, labs, and radiology systems. Trainers gathered information from trainees. Some used the “Net Obey” application to connect all network devices to facilitate data collection. Some organizations maintained intranets and web portals to collect all work-related information, especially for employees (e.g., POMS for the Human Resource and Student Information System for student information). Some participants (e.g., those working for the Central Agency for Public Tenders) needed to gather information from other institutions using the Government-to-Government system (G2G). Most participants indicated a preference for gathering information using social media, websites, similar examples of other work, and previous document versions.
Table 2 summarizes the information types participants reported as needed to perform work tasks. All participants listed personal appointments, schedules, and noteworthy dates as frequently used information types. Most dealt with reports and text documents, but draft works constituted 81%. Social workers needed full personal information from students and parents to contact them when needed. Health information specialists needed to maintain the patient records. Software programmers kept records in secure systems handled by their organizations, especially sensitive information such as IDs, passwords, and bank accounts. Other types of information included website links, e-mail addresses, reminders, photos, statistics, mailing addresses, and sound and video recordings. Depending on the current role, knowledge workers used the available types of information to make better decisions for their managers.
A variety of information types were used depending on the work situation, but all participants used appointments, schedules, and noteworthy dates to manage work tasks.
4.2 Keeping Information
In response to a question about information saved for future use, most participants said that practical experience guided their decisions on the information that needed to be retained. For example, this included practical work for teaching, internship materials, training programs, directories, and conferences. Teachers retained information on teaching strategies, active learning, classes, and time management. One teacher stated the following: “I never delete data and I keep everything.” Lush (2014) mentioned two controversial directions for keeping information during PIM (i.e., “keep everything” vs. “keep nothing”). “Keeping everything” results from the desire to retain information that may be useful later, while “keeping nothing” is related to the concern that most information may never be used. Social workers kept personal information and student health records. On the other hand, health information specialist retained information about causes of death, newborns, and diseases. One health information specialist stated the following: “Since the 1960s we do not delete the health records.” Software programmers were required to ensure that saved information was not redundant and in good condition. One software programmer stated the following: “We have to check the Antivirus software and we download programs for the employees from our department.”
Knowledge workers in this study used several methods of retaining information (Table 3). Saving to the desktop, personal folders, or shared drives were the most common methods. A total of 85% of all participants stored information on external services, while 81% e-mailed themselves. This corroborates the findings of Bota et al. (2017) in which participants mainly sent themselves reminders and to-do lists. In addition, 81% of all participants saved information to cloud services (e.g., Google Drive, Dropbox, or iCloud). However, teachers did not use school group drives. This corroborates the findings of Diekema and Olsen (2011). A total of 73% of all participants bookmarked websites or added items to favorites lists. This differed from the findings of a study conducted three years earlier by Chaudhry, Rehman, and Al-Sughair (2015).
The least-common methods used to retain information were saving to web pages and pasting website addresses (i.e., URLs) into documents, respectively. Other keeping methods depended on the work itself. For example, an information specialist mentioned Refworks for keeping article citations. Software programmers used the Footprint system to keep troubleshooting information. Other participants also reported using systems for database maintenance, including Oracle, Tandem for employees, Citrex, G2G, Power Campus for registration, Mendeley, and SAAB for employees.
Participants were also asked about their experiences with information keeping methods. All were happy to use such methods because they served as document archives. For example, an information specialist motioned that such information keeping methods made it “easier, less time, less effort, to get the information directly.” One teacher said that such methods were “very useful, fast, easy, and most suitable for my job.” Some still relied on traditional methods (e.g., saving to flash memory). However, the majority preferred to learn new methods.
The most commonly used information keeping device was the desktop computer. This corroborated with the findings of Molazadeh et al. (2017). E-mail, mobile phones, and laptops were also popular (Table 4). Participants also used devices such flash memory and external hard drives; the least common device was the tablet. One information specialist stated the following: “I keep three copies in hard disc, email, and Dropbox for backup because I am afraid of technology and it is not reliable for storage.” Other organizations offered cloud storage to encourage users to preserve hardware storage. For example, one administrative assistant stated the following: “we use One Drive so we do not need external hardware.” In addition, one trainer stated the following: “If you store it on flash, there is a chance to be lost. However, if you store it on Dropbox it will be stored forever.” However, one administrative assistant stated the following drawback: “I love shared drive because it is easy to share, but when the system is down, you are lost!” Most participants used the cloud because it was easy to access and more secure than the desktop computer. These findings support the results of a study by Kearns et al. (2014).
4.3 Organizing Information
All participants used folders to organize information, but arranging methods varied. The top method for organizing folders involved subject/topic labeling and using meaningful file and folder names. Studies by Majid et al. (2013) and Chaudhry, Rehman, and Al-Sughair (2015) mentioned that proper file and folder-naming could solve problems of information fragmentation. A total of 77% of all participants organized folders according to time period. Most chronologically divided their folders according to month, semester, academic period, and financial year. Less than half of all respondents organized their folders by project name, document type, file format, or status/version (Table 5). These results differ significantly from those of Chaudhry, Rehman, and Al-Sughair (2015). Knowledge workers are now aware of the importance of using folders for structural organization.
The use of folders to organize e-documents can facilitate organizational workflow. Participants indicated that they could easily retrieve information if folders were organized effectively.
4.4 Managing Information
Participants reported feelings of happiness after clean-up exercises because files were then easier to find. Only one participant considered file-cleaning a waste of time, stating that there were better things to do. A total of 69% of all participants deleted files/folders when they fell into disuse, and 58% immediately filed documents into folders (Table 6). Almost half of all participants regularly cleaned their desktops. About one-third of all participants cleaned their desktops subsequent to a problem, while another third cleaned files and folders periodically, and the remaining third cleaned their desktops upon work completion.
More than 75% of all participants were aware of the importance of converting e-mail messages into task and calendar formats (77%) to better organize information (Table 7). In addition, 65% of all participants performed periodic reviews to delete unnecessary messages. “Tag and flag” messages were used by 62% of all participants, who said that tag and flag was not only used for e-mail messages, but with other social media applications. A total of 58% of all respondents deleted, delegated, or deferred messages for quick disposal. Half of all participants left all e-mail messages in inboxes, while the rest used structured folders to organize and categorize messages.
Most participants used e-mail to identify personal contacts and networks. They also properly organized contacts using e-mail features. Almost half maintained an updated list of contacts using e-mail features, shared information on social networking sites, and looked for people with similar interests at conferences. Only 42% of all participants recorded the locations of important contacts. Only 31% reviewed contact interactions. Less than 25% of all participants followed or re-tweeted their contacts using Twitter (Table 8).
4.5 Obstacles
A total of 85% of all participants viewed information overload as a major obstacle. This is because their work-related information was of a large scale (Table 9). A total of 77% of all participants said this sometimes led to information anxiety. The second most commonly reported obstacle was information fragmentation (81%). Many participants were not aware of this term, but described it according to the definition. Some stated that they had multiple work devices, which made it difficult to have them available at all times. About 70% said they faced the problem of hybridization (i.e., information in combined digital and traditional formats). One software programmer stated the following: “Now everything is digitized and archived in my organization so we do not face this problem.” Most participants (70%) said they had problems determining the future value of information. Most administrative assistants used a cloud service to avoid the problem of fragmentation, but faced problems when systems were unavailable (Table 9). Otopah and Dadzie (2013) also reported that inadequate skills, information fragmentation, inappropriate habits, and imperfect memories were obstacles. These were also mentioned by this study’s participants.
In addition to those on the list, teachers mentioned other obstacles (e.g., schools did not provide Internet access, lack of school e-mail domains, and limited time for learning about new PIM tools). One information specialist mentioned a problem in which document language sometimes caused misunderstanding during communicating. One of the software programmers had problems with hacking and difficulty identifying duplicates. One trainer stated the following: “I have many flashes and problems related to the virus.” Health information specialists said there was no standardized way to keep information in the organization.
4.6 Tools
Participants reported using the following PIM tools:
∙ PIM Tools (e.g., calendars, tasks, and schedules) (100%)
∙ E-mail Management Tools (92%)
∙ Cloud Services (e.g., Google Drive, Dropbox, OneDrive, iCloud) (85%)
∙ Social Networking Tools (54%)
∙ Others (19%)
All participants reported using PIM tools such as calendars, tasks, and schedules. Most used e-mail management tools and cloud services (e.g., Google Drive, Dropbox, OneDrive, and iCloud) (92% and 85%, respectively). More than half used social networking tools while working. For example, information professionals frequently used LinkedIn, while teachers mainly used Telegram, Pinterest, and WhatsApp Groups. Some trainers used myU and Edmo to contact trainees during training courses. Organizations also used other social media accounts (e.g., Snapchat, Instagram, Twitter, YouTube, and Facebook). Teachers mentioned using the Teacher Kit Application, Checklist Application, and Refworks. Other note applications included Pinbaord.in, Instapaper, and Evernote.
4.7 Re-finding Information
Participants mainly searched by keyword and browsed through folder structures to re-find information (96%). This was followed by using their own memories and scanning the desktop screen (85% and 77%, respectively). About 70% searched for files using tags, labels, and bookmarks. Only 27% retrieved information on their mobile devices using Siri or Ask Google. One teacher demonstrated using an Android device to re-find information, as follows: “OK Google! Start to do list.” Some information specialists mentioned using iPhones to re-find information by asking Siri place calls (Table 10). The re-finding methods ascertained in this study corroborated with results by Chaudhry, Rehman, and Al-Sughair (2015). However, the bookmarking method was used less frequently and new techniques (e.g., Siri and Ask Google) were available in this study.
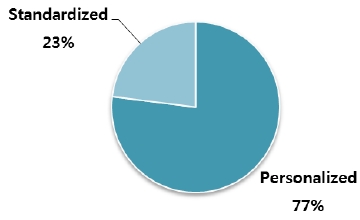
Nearly 75% of all participants used PIM techniques, while less than 25% used standard techniques (Fig. 2).
Mas, Maurel, and Alberts (2011) stated that many users preferred their own organizational systems. This is because institutional systems are sometimes too generic and rigid. Most participants in this study used their own information management methods, including personalized ways of selecting meaningful folder names, organizing files using their own management methods, and storing information on the most convenient devices. Other participants kept information using standard methods (e.g., organizational shared drives or web portals). A study by Creegan (2017) mentioned that, although some participants used an institutional shared drive within an overarching organizational system, most used their own systems of organization. This contributes to a shared organizational system that is only superficially standardized.
4.8 Internet Use
Majid et al. (2010) mentioned many Internet services that could be used to maintain personal information. Most participants used these services and agreed that the Internet was helpful when performing PIM because information was available anywhere and at all times. It could thus easily be shared while storage capacity was less of an issue. However, one administrative assistant noted the following: “I am paying for the storage in my Dropbox.” Integrated search features also allow users to quickly and accurately retrieve information. One information specialist stated the following: “I have to be a good researcher because Internet cannot know what is in my mind.” A total of 85% of all participants mentioned that the uploading and downloading speeds for personal information items transferred over the Internet was satisfactory. However, this largely depended on local wi-fi capacity, as mentioned by one trainer. A total of 81% of all participants said that using an Internet service as a central storage location reduced the need to maintain multiple copies because such stored copies were more stable than those retained on desktop computers. Digital items were also easily organized. Only 12% of all participants said that most Internet services were trustworthy repositories for private and confidential information. As such, one teacher stated the following: “Most of the time, yes, but it depends.” On the other hand, 85% of all participants agreed that Internet services were only suitable for non-sensitive information (Table 11). However, one teacher stated the following: “I save everything apart from the Internet as soon as possible.”
All participants were convinced that Internet services facilitated information management. The Internet was more convenient, but participants had concerns over privacy.
4.9 Privacy and Security
Participants provided some security strategy tips while using Internet services. Most controlled how much personal information was shared in addition to the intended audience. They did not often place personal information into Internet service repositories, and usually only stored items they wished to share with others. Only three participants thought Internet services could adequately protect their information from fraud, vandalism, break-ins, or theft. Participants generally had reservations about Internet service privacy, but could not ignore their importance for providing useful platforms with which to save digital information. These results support the findings of Majid et al. (2010). Results are available in Table 12.
4.10 Mobile Application Use
All participants reported using mobile devices to store personal information, including e-mails and social media accounts. Such information was primarily intended for sharing. One trainer said they used online meetings and Live Instagram to share information. Some participants felt disorganized when forgetting to carry their phones. For example, one social worker stated the following: “My mobile contains everything!” One information specialist similarly stated the following: “I store everything on my phone and I manage my bank accounts, emails, contacts, photos, eBooks, tasks, default note, calendars, reminders, and to-do list.” In addition, one administrative assistant stated the following: “I used the default notes in my iPhone to store passwords for every account and I used photos to save and capture important stuff.” One information specialist used a personal phone to manage “bank information and personal budget.” Some participants mentioned the ability to open multiple e-mail addresses in one inbox in the default mobile e-mail application. They were thus able to better manage their e-mail correspondences.
Some participants used the default “Files” application on the iPhone. One software programmer stated the following: “I put my family passports on files application on my iPhone’s File application.” Participants who used Dropbox downloaded the application to their phones. One teacher stated the following: “I use Dropbox on my device and I manage folders in it. I upload files from email to Dropbox and vice versa.” One information specialist similarly stated the following: “I use Dropbox on my personal device (iPhone), which is connected directly to my PC. Whatever I save, manage, update on my PC through Dropbox, automatically I can see on my mobile.”
Some participants used mobile applications to manage personal information (e.g., Wonderlist, Do It, and iExpand) and move images from mobile devices to computers and vice-versa. One teacher stated the following: “All teachers in Kuwait are in Telegram, I can contact with the admin of the group to contact any member in the group.” It was thus mainly used to share educational materials. Only one teacher stated the following: “I am old fashioned, I like PC more, but I use the mobile for using my email and social media for normal sharing.”
5. Conclusion
Knowledge workers in Kuwait use and organize many types of information (e.g., appointments, schedules, noteworthy dates, reminders, reports, text documents, personal identification information, website links, e-mail addresses, draft works, photos, statistics, and sound and video recordings). These workers also gather information from online databases, journals, social media platforms, websites, intranets and web portals, colleagues, and archives. They keep information on their computer desktops, shared drives, external services, in personal folders, e-mails to themselves, clouds, bookmark lists, websites or favorites lists. The most common device used to retain information is the desktop computer. Other areas include e-mail messages, mobile phones, laptops, flash memory, external hard drives, and tablets. Knowledge workers organize information using differently categorized folders labelled according to subject/topic, time, project, document type, file format, status/version, and geographical region. Most of these workers reported feelings of happiness after performing clean-up exercises to make files easier to find.
Knowledge workers periodically review information spaces to delete unnecessary messages and documents and use tags and folders to organize messages. They also use e-mail correspondence to build contacts and maintain updated lists. The preferred methods of re-finding information were keyword searches, browsing through folder structures, and using one’s own memory. However, knowledge workers are confronted with obstacles when performing these tasks and may experience information overload. Some obstacles include information fragmentation, information anxiety, hybridized material formats, and difficulty determining the future value of information. Most were active social media users on mobile devices, which they also used to manage personal information. Some used Siri or Ask Google to retrieve information. These users also applied e-mail management tools, cloud services, and social networking tools when performing PIM.
The Internet is also a useful PIM resource. It makes personal digital information available anywhere and at any time in addition to offering ample storage capacity. However, users reported privacy concerns about storing sensitive information on the Internet.
This study was limited to one group of knowledge workers who were graduates of the Department of Information Studies at Kuwait University. However, these participants worked in different organizations and performed a variety of roles. This study’s findings are thus comprehensive in content and cover many work situations. Future studies can add to these data by including different groups of knowledge workers. Other data collection techniques should also be implemented, including focus groups to provide additional information about PIM tools and practices.
References
- Al-Omar, M., & Cox, A. M., (2016), Scholars’ research-related personal information collections: A study of education and health researchers in a Kuwaiti University, Aslib Journal of Information Management, 68(2), p155-173.
- Bota, H., Bennett, P. N., Awadallah, A. H., & Dumais, S. T., (2017, March), Self-Es: the role of emails-to-self in personal information management, In Proceedings of the 2017 Conference on Conference Human Information Interaction and Retrieval, p205-214, ACM.
- Chaudhry, A., Rehman, S., & Al-Sughair, L., (2015), Personal information management practices in the Kuwaiti corporate sector, Malaysian Journal of Library & Information Science, 20(3), p27-42.
-
Chaudhry, A., Rehman, S., & Al-Sughair, L., (2016), Using personal information management to strengthen information literacy at work, International Journal for e-Learning Security, 5(1), p421-428.
[https://doi.org/10.20533/ijels.2046.4568.2015.0054]

- Creegan, T. D., (2017), A study of the personal information management practices of Librarians, (Master’s thesis), Retrieved from http://researcharchive.vuw.ac.nz/xmlui/bitstream/handle/10063/6625/paper_access.pdf?sequence=1.
-
Diekema, A. R., & Olsen, M. W., (2011), Personal information management practices of teachers, Proceedings of the Association for Information Science and Technology, 48(1), p1-10.
[https://doi.org/10.1002/meet.2011.14504801189]

-
Divya, L. R., & Sudhier, K. G., (2016), Attitude of personal information management among research scholars: A study on University of Kerala, Library Herald, 54(1), p115-125.
[https://doi.org/10.5958/0976-2469.2016.00009.9]

-
Kearns, L. R., Frey, B. A., Tomer, C., & Alman, S., (2014), A study of personal information management strategies for online faculty, Journal of Asynchronous Learning Networks, 18(1).
[https://doi.org/10.24059/olj.v18i1.296]

-
Kim, Y., & Hur, Y., (2016), The effect of personal information management tool usage, personal information sensitivity, and information ethics awareness on information security awareness, International Journal of Social Welfare Promotion and Management, 3(1), p239-246.
[https://doi.org/10.21742/ijswpm.2016.3.38]

- Lush, A., (2014), Fundamental personal information management activities–organization, finding and keeping: A literature review, The Australian Library Journal, 63(1), p45-51.
-
Majid, S., Chang, Y. K., Foo, S., Mokhtar, I. A., Theng, Y. L., & Zhang, X., (2013, October), Strengthening information literacy competencies through incorporating personal information management skills, In European Conference on Information Literacy, p331-337, Springer, Cham.
[https://doi.org/10.1007/978-3-319-03919-0_43]

-
Majid, S., San, M. M., Tun, S. T. N., & Zar, T., (2010, September), Using Internet services for personal information management, In International Symposium on Information Management in a Changing World, p110-119, Springer, Berlin, Heidelberg.
[https://doi.org/10.1007/978-3-642-16032-5_10]

- Mas, S., Maurel, D., & Alberts, I., (2011), Applying faceted classification to the personal organization of electronic records: Insights into the user experience, Archivaria, 72, p29-59.
-
Mizrachi, D., & Bates, M. J., (2013), Undergraduates’ personal academic information management and the consideration of time and task-urgency, Journal of the Association for Information Science and Technology, 64(8), p1590-1607.
[https://doi.org/10.1002/asi.22849]

- Molazadeh, M., Zeinali, A., Geraily, G., & Shirazi, A., (2017), Investigating the use of personal information management strategies by faculty members of three medical sciences universities in Iran, MIER Journal of Educational Studies, Trends and Practices, 7(1), p107-120.
- Otopah, F. O., & Dadzie, P., (2013), Personal information management practices of students and its implications for library services, Aslib Proceedings, 65(2), p143-160.
-
Zhou, L., Mohammed, A. S., & Zhang, D., (2012), Mobile personal information management agent: Supporting natural language interface and application integration, Information Processing & Management, 48(1), p23-31.
[https://doi.org/10.1016/j.ipm.2011.08.008]

Appendix
6. Appendices
[Appendix-A] Interview Guide
What is the overall purpose of the job?
What sort of tasks do you have to do?
∙ E-mail Addresses
∙ Website Links
∙ Text Documents
∙ Reports
∙ Mailing Addresses
∙ Photos
∙ Draft Works - work documents for continuation at home or elsewhere
∙ Statistics
∙ Sound and Video Recordings
∙ Schedules
∙ Reminders
∙ Noteworthy Dates
∙ Appointments
∙ Personal Identification Information (e.g. Passport, IDs and Passwords, and Bank Accounts)
∙ Other
When you receive needed information, do you delete this after finishing the tasks or keep/save some of the information for the future use?
What type of information is kept for future use?
What devices are used to store information? (Desktop Computer-Laptop-Tablet-External Hard Drive-Flash Memory-Mobile Phone-E-mail)
What methods are used?
∙ Bookmark website or add a favorite
∙ Save to desktop, personal folder, or shared drive
∙ E-mail to self
∙ Store via external service
∙ Paste the website address (URL) into a document
∙ Save the web page
∙ Save to cloud (Google Drive, Dropbox, OneDrive, iCloud)
∙ Other
What is your experience with the methods of saving/keeping information? (Happy-Preferences-To understands past decisions-An archive of information used in the past that might be used again)
ⅰ. Using Folders
∙ Organization Structure
∙ Document Type
∙ File Format
∙ Geographic Region
∙ Subject/Topic
∙ Project
∙ Status/Version
∙ Meaningful File and Folder Names
∙ Time
∙ Other
ⅰ. Using E-mail
∙ Leave all mails in the inbox
∙ Structure folders to organize messages
∙ Review periodically to delete unnecessary messages
∙ Convert messages into actions (e.g., tasks and calendars)
∙ Choose messages to delete, delegate, or defer for quick disposal
∙ Categorize messages for quick future retrieval
∙ Tag and flag messages
ⅰ. Using tagging/labeling
∙ Meaningful tagging/labeling descriptions
ⅰ. Contacts
∙ Use E-mail to identify personal contacts and networks
∙ Maintain an updated list of contacts using e-mail features
∙ Share information on social networking sites
∙ Keep business cards of people
∙ Look for people with similar interests at conferences
∙ Record the location of important contacts
∙ Follow and re-tweet my contacts using Twitter
∙ Review the frequency of interaction with my contacts
∙ I regularly clean up my desktop (e.g., once a week)
∙ I only clean up my desktop when something goes wrong
∙ I clean up my desktop when the work or project is completed
∙ I delete files/folders when I find they have no use anymore
∙ I file documents into folders immediately
∙ I clean up file documents into folders periodically
∙ I clean up my files and folders when I have time
∙ I feel happy after a clean-up exercise because it makes files easier to find in future
∙ It is a waste of time to clean files as I have better things to do
∙ Other
∙ Fragmentation
∙ Information Anxiety
∙ Information Overload
∙ Huge in Scale
∙ Hybrid Materials (Traditional and Electronic Formats).
∙ Determine the Future Value of Information
∙ Other
∙ PIM Tools (e.g., calendars, tasks, and schedules)
∙ Pinbaord.in
∙ Instapaper
∙ Evernote
∙ Simplenote and Notational Velocity (Mac)
∙ E-Mail Management Tools
∙ Cloud Services (e.g., Google Drive, Dropbox, OneDrive, iCloud)
∙ Social Networking Tools
∙ Other
How often you needed the information for the saved resources?
What approaches you used to re-find?
∙ Search by keyword
∙ Browse through folder structure
∙ Access through bookmark
∙ Search file names by remembering tags or labels
∙ Use own memory
∙ Use Siri for iPhone or Ask Google for Android.
∙ Scan the desktop screen
Do those tools and techniques help?
How much of your information management still relies on your memory to know where things are?
How much of your information management is standardized and how much is personalized?
Reasons for using Internet services for storing personal information items:
∙ Internet services make my personal digital information items available anywhere and at anytime
∙ Most Internet services offer enough storage capacity for storing my personal digital information items
∙ Using an Internet service as a central storage location reduces the need to maintain multiple copies of my items
∙ Most Internet services are more stable than my own desktop computer in terms of system reliability
∙ Uploading and downloading speeds involving personal information transfers over the Internet are satisfactory
∙ Personal information items can easily and effectively organized by using Internet service features
∙ Internet search features allow me to retrieve my information quickly and accurately
∙ Personal digital information items can easily be shared with others
∙ Most Internet services are trust-worthy for private and confidential information transfers
∙ Internet services are only suitable for non- sensitive information
∙ I do not place sensitive personal information into Internet services storage
∙ I only place personal information that I wish to share with others into Internet service storage
∙ Internet services can adequately protect my information from frauds, vandalism, break-ins, and theft
∙ I can control the degree to which I share personal information with my intended audience
Bashaer AlRukaibani
E-mail: bashaer.faham@gmail.comBashaer AlRukaibani did Mater of Information Studies from Kuwait University. She is presently working as a Software Programmer at the Ministry of Communication in Kuwait. She was an intern at Kuwait University Center of Information Systems in 2014. Her current research interests are in the areas of information management, digital learning, and social media.
Abdus Sattar Chaudhry
E-mail: a.chaudhry@ku.edu.kwAbdus Sattar Chaudhry did Master from University of Hawaii and PhD from University of Illinois at Urbana-Champaign. He is currently a professor at the Department of Information Studies at Kuwait University. He has earlier taught at Nanyang Technological University of Singapore. His current research interest include organization and management of information and knowledge.